Bluetooth hack affects 20 million amazon echo and Google Home devices
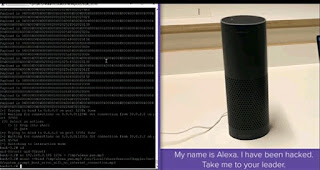
#&# computer experts Remember BlueBorne? A series of recently disclosed critical Bluetooth flaws that affect billions of Android, iOS, Windows and Linux devices have now been discovered in millions of AI-based voice-activated personal assistants, including Google Home and Amazon Echo . As estimated during the discovery of this devastating threat, several IoT and smart devices whose operating systems are often updated less frequently than smartphones and desktops are also vulnerable to BlueBorne. BlueBorne is the name given to the sophisticated attack exploiting a total of eight Bluetooth implementation vulnerabilities that allow attackers within the range of the targeted devices to run malicious code, steal sensitive information, take complete control, and launch man-in-the-middle attacks. What's worse? Triggering the BlueBorne exploit doesn't require victims to click any link or open any file—all without requiring user interaction. Also, most security produ